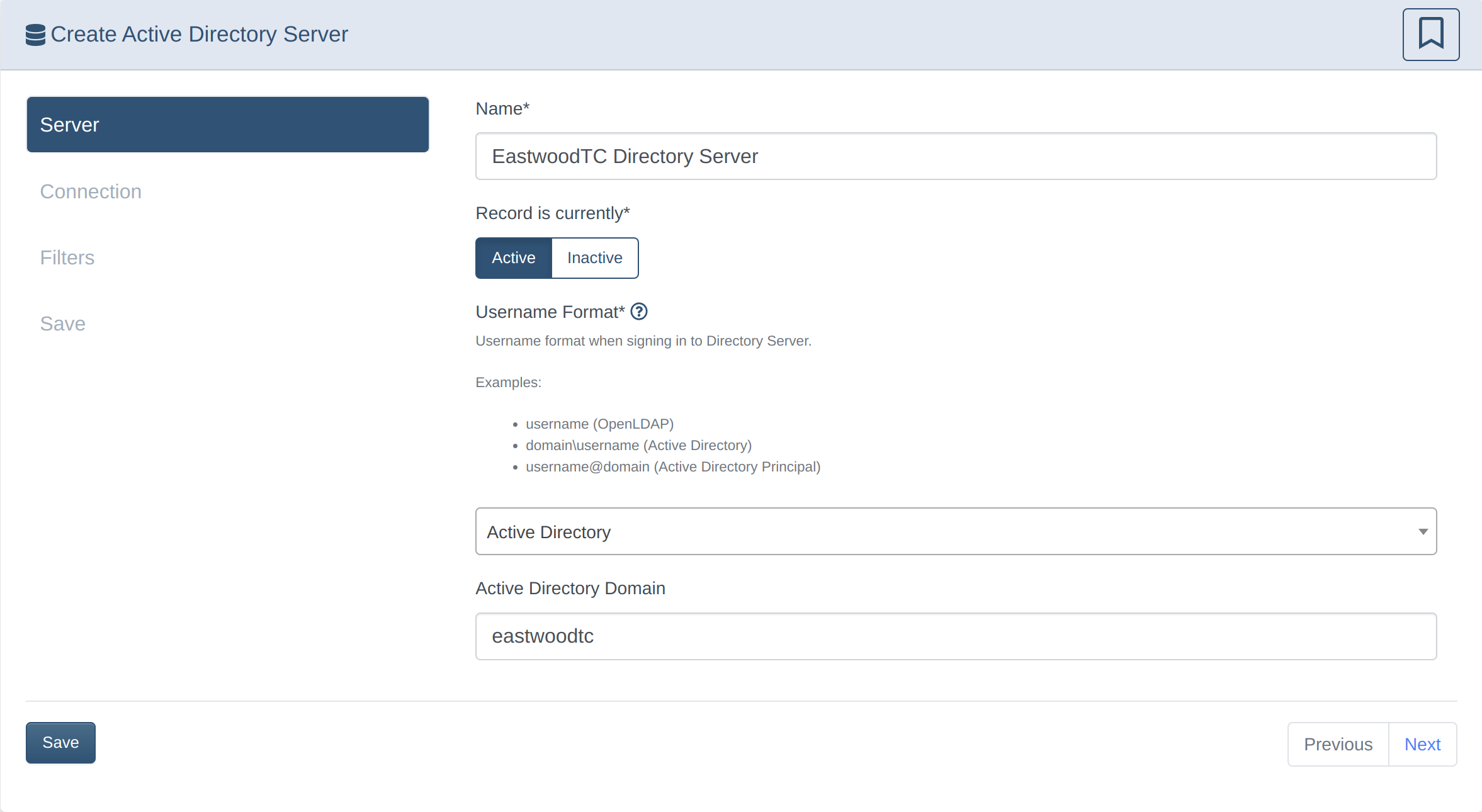
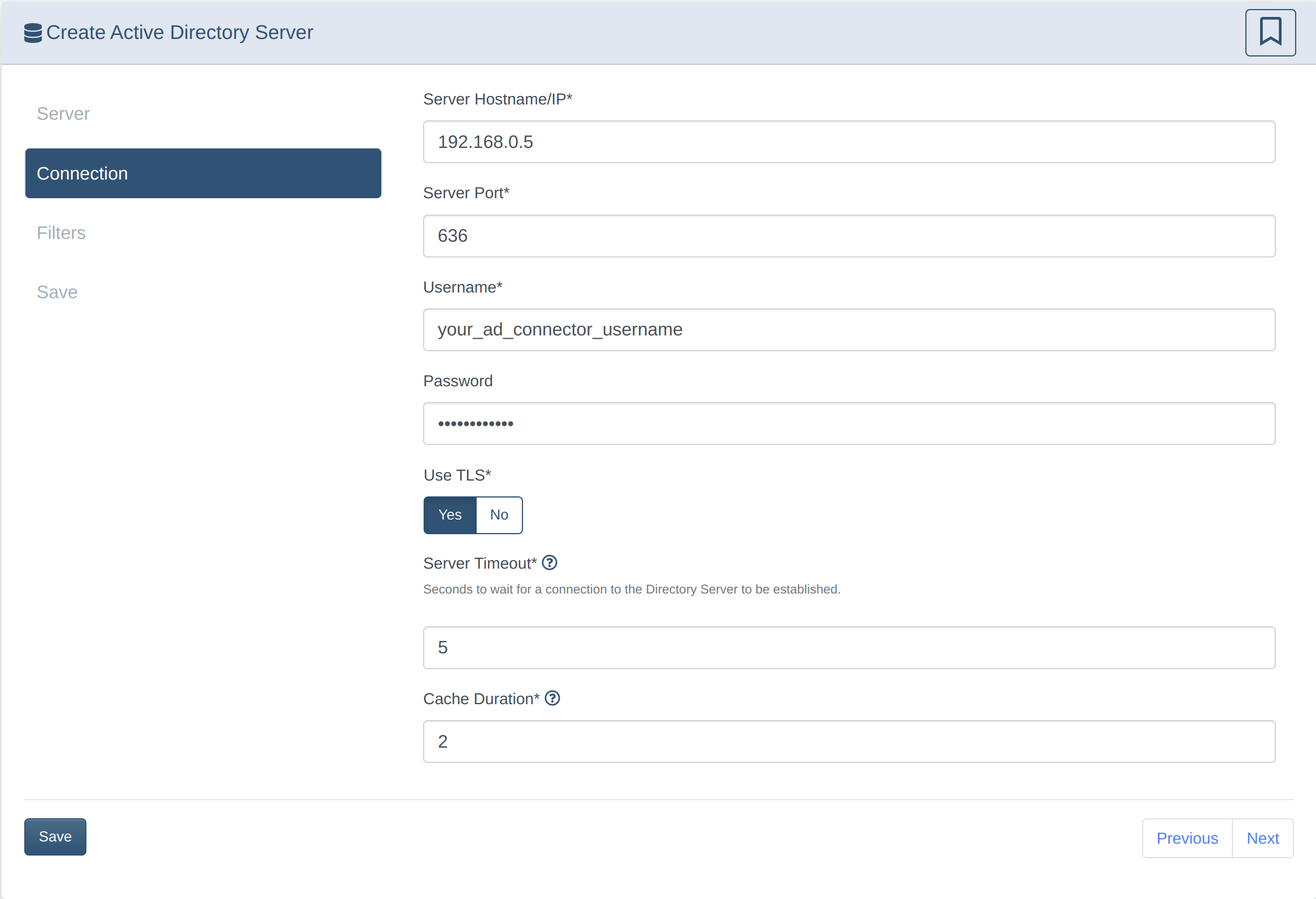
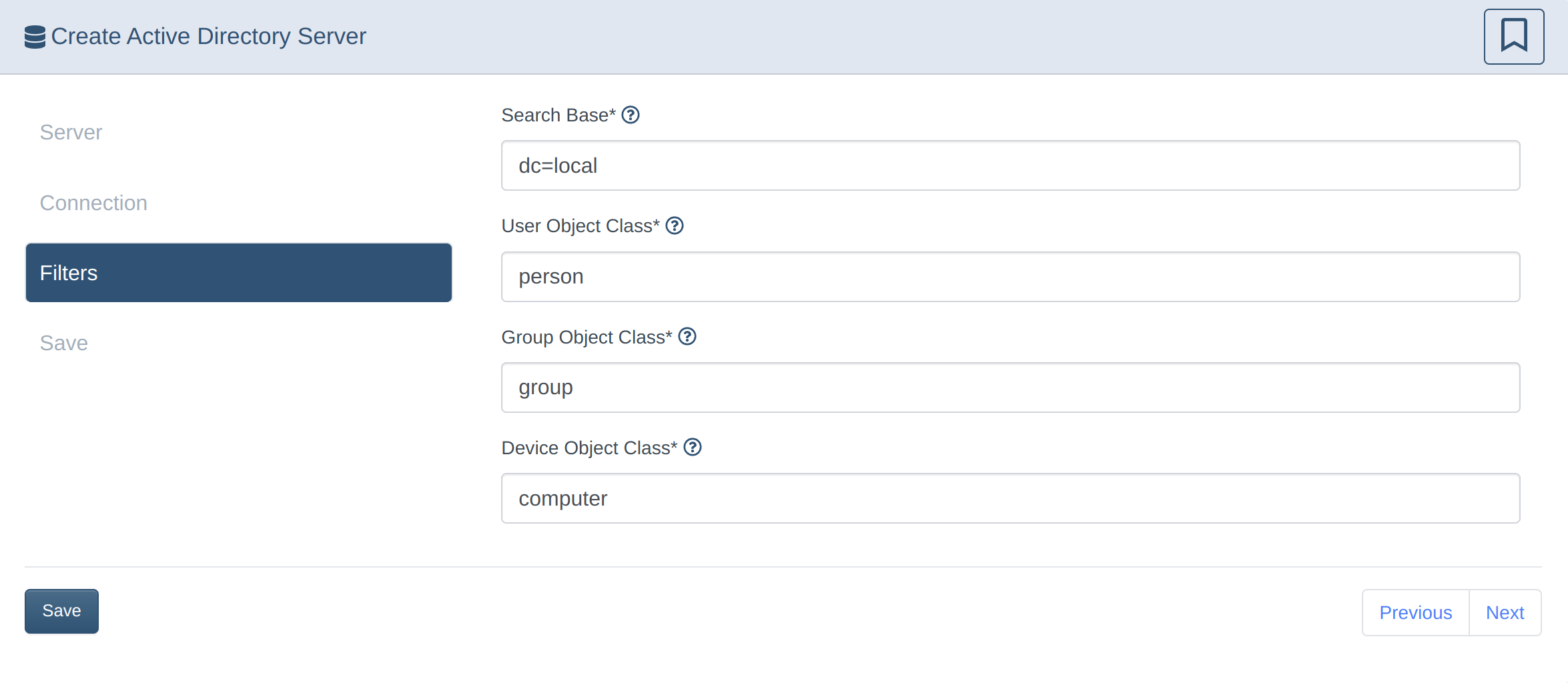
Set up Active Directory sync
Synchronize your Active Directory Users and Groups to enable content filter policy assignment to AD-managed people groups (rather than network devices via IP address).
1. Configure your AD server for synchronization
- Create a User that has access to the user and groups database (should Not be a domain admin for security reasons)
- Ensure your AD server allows LDAPS on 636 or plaintext access on port 389
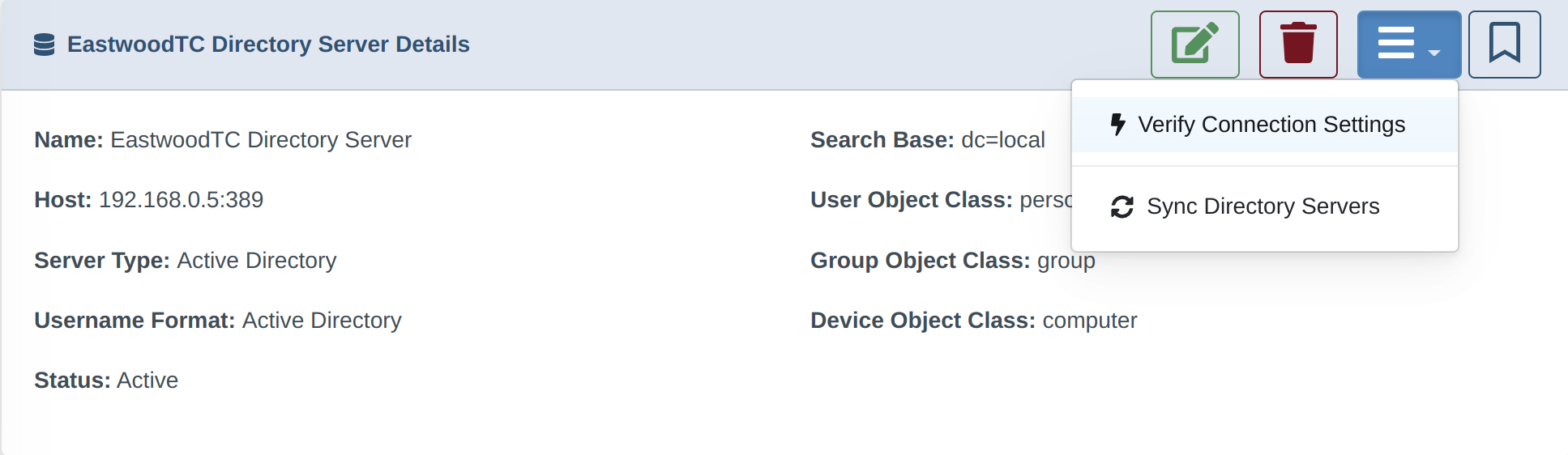
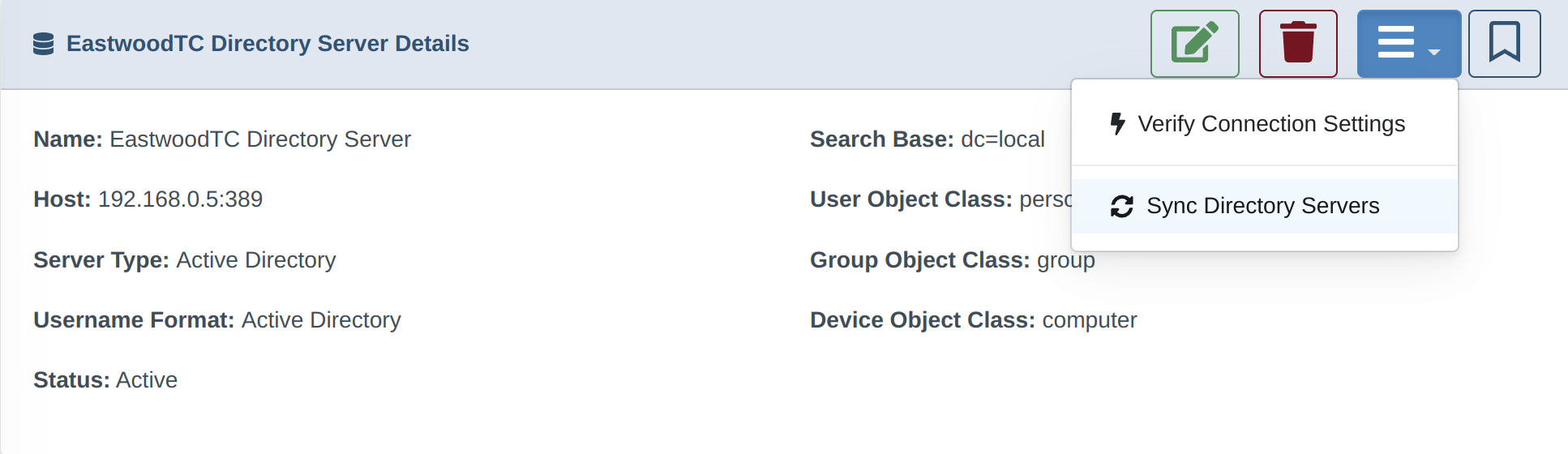
2. Configure the DrawBridge for AD Sync
4. Next Steps
This how-to guide is the prerequisite procedure to setting up filter policies for Directory Groups. For further instructions, see the articles:
- Configure Proxy User Groups
- Assign an Access Policy to a Proxy User Group
Troubleshooting Resources
-
Use the Directory Service event log on your Windows Server to diagnose AD-sync authentication issues.
-
Locate unsecure LDAP requests: (Source: Spiceworks Forum)
- On all of your DC's, look at the Directory Service event log.
- Search for event 2887.
- If exists that means you still have clients using non-secure LDAP requests and how many.
- If you change the diagnosting logging level for LDAP, you can find the IP address of these clients:
HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics- Change the value of
16 LDAP Interface Eventsfrom0to2.- After the change you should see event 2889 logged whenever one of these requests come in.